Mobile Device Management Software
One solution to secure your entire fleet
Strengthen security and streamline device management with the only MDM software to provide real-time access to native user and device data.














Employee graph
Single source of truth for all your devices
With native user and device data made available out of the box, you can build hyper-granular policies for total control over device security – no SCIM integrations or manual data pulls required.
PULL REQUESTS
Department
Location

Compliance certifications

Employment status

Background Checks

PULL REQUESTS
Department
Location

Compliance certifications

Employment status

Background Checks

MDM status
CPU Type

Jira issue
MANAGER

Device order
Detected threats

Manufacturer

Encryption Status
MDM status
CPU Type

Jira issue
MANAGER

Device order
Detected threats

Manufacturer

Encryption Status
LEVEL
Model year

DIRECT REPORTS
NAME

Screen size

Operating System
BATTERY HEALTH
LEVEL

Purchase date
DIRECT REPORTS
LEVEL
Model year

DIRECT REPORTS
NAME

Screen size

Operating System
BATTERY HEALTH
LEVEL

Purchase date
DIRECT REPORTS

Total visibility
Get real-time insight on your security posture with device and user data at your fingertips.

Automated lifecycle management
Streamline device management with automations for the entire lifecycle of Apple and Windows devices.

User-driven security policies
Build and enforce custom security policies based on hundreds of user and device attributes.
Security
Friction-free security
Rippling gives you granular security controls across your entire fleet and user lifecycle – from custom policies and device monitoring, to rich reports and threat management.
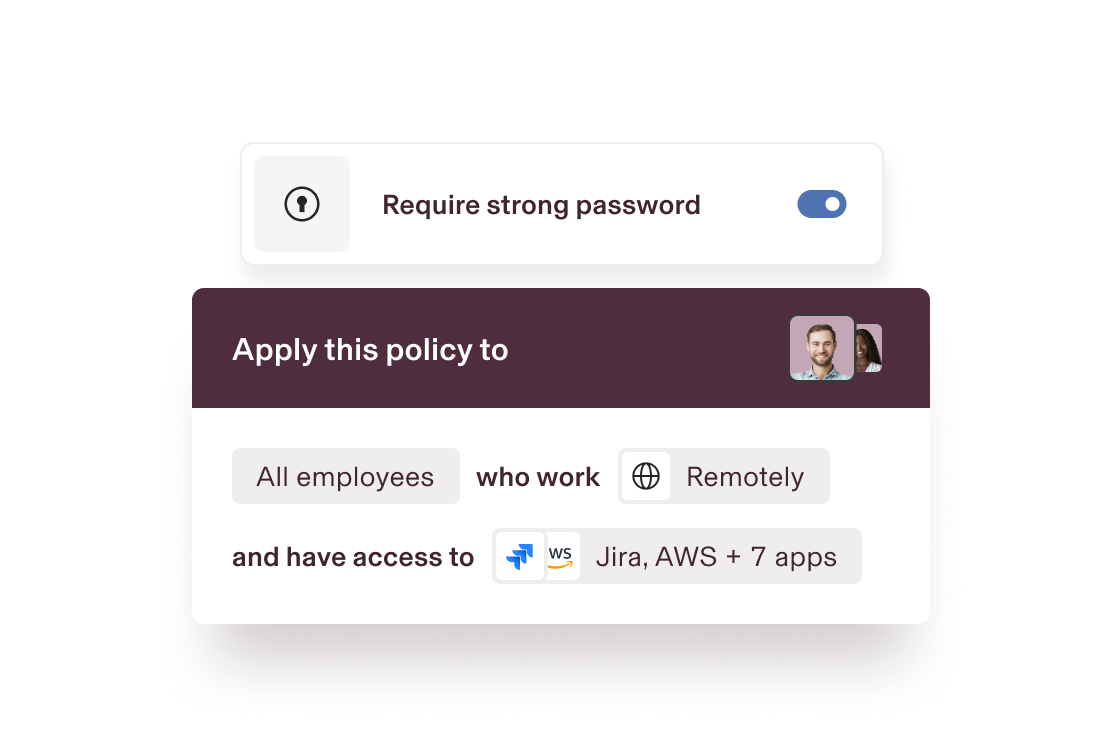
Dynamic security policies
Custom security policies based on user and device attributes automatically update for a stronger security posture across your org.
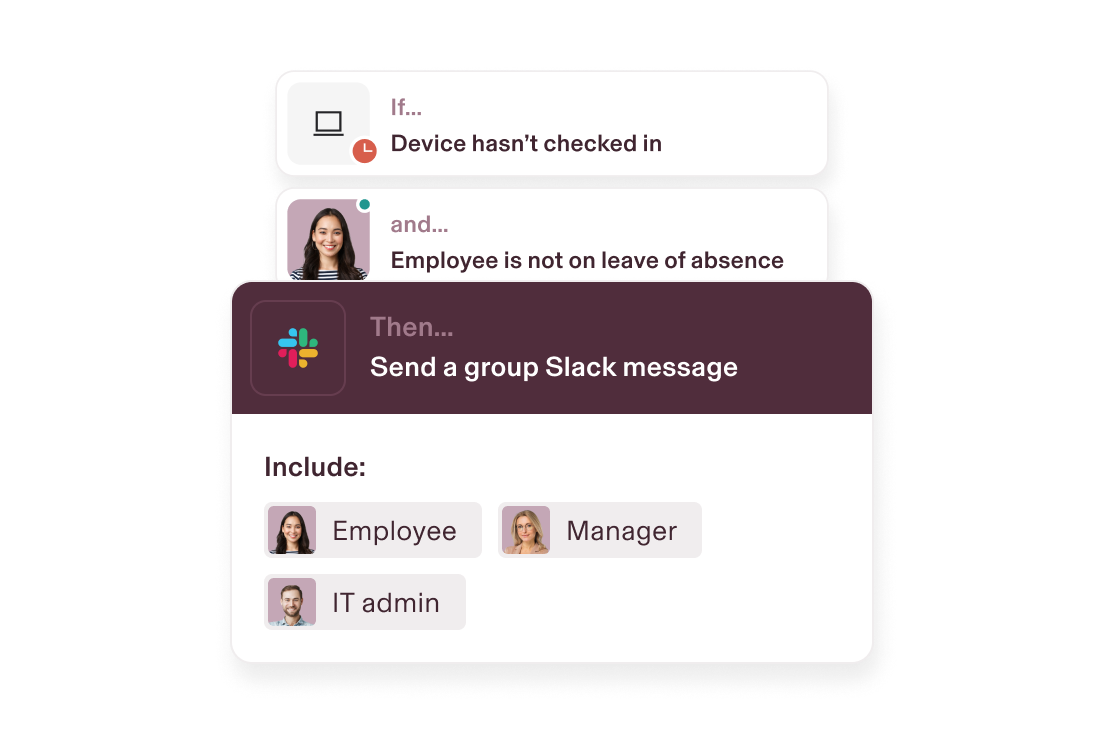
Automated device monitoring
Stay on top of security. Custom workflows will automatically notify you of any security threats – no manual device checks or data pulls required.
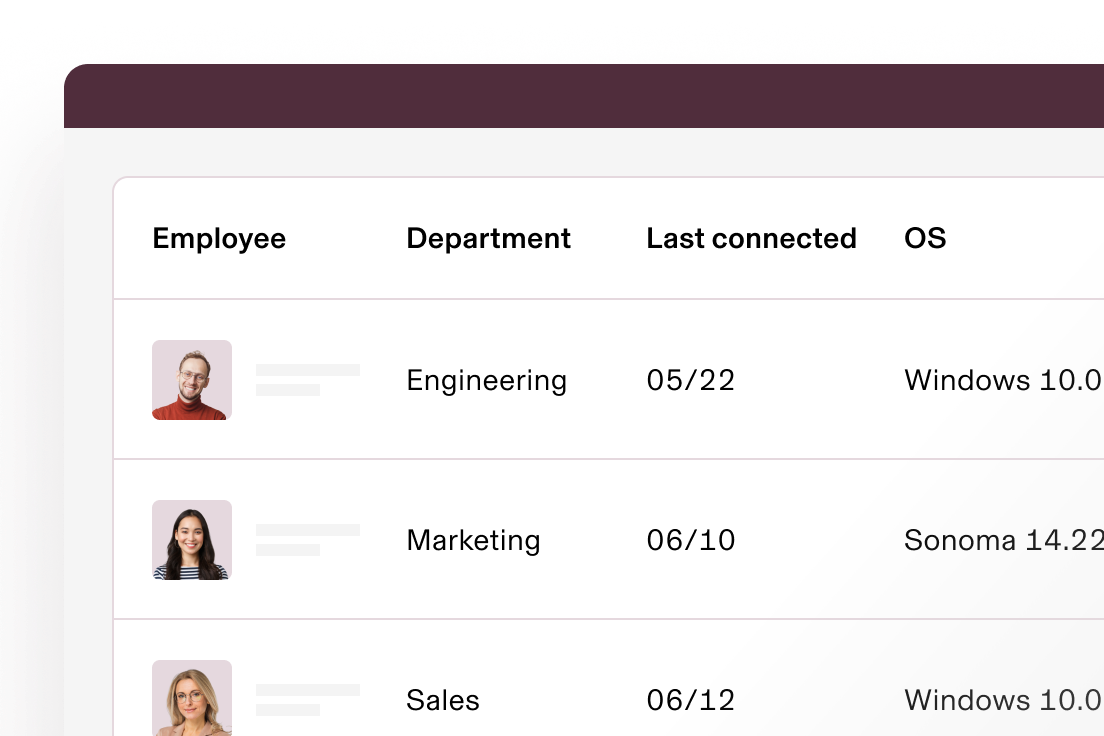
Full visibility and reporting
Point-and-click custom reports based on rich user and device data makes it easy to understand your security status and pull audit data.
Zero-touch deployment
SentinelOne is deeply integrated with Rippling to ensure that all devices are secured with best-in-class endpoint protection, automatically.

ONBOARDING
Devices done right on day one
Custom approval polices and workflows based on real-time data keep you in control and in sync with HR – letting you onboard new employees as hands-on or hands-off as you want.
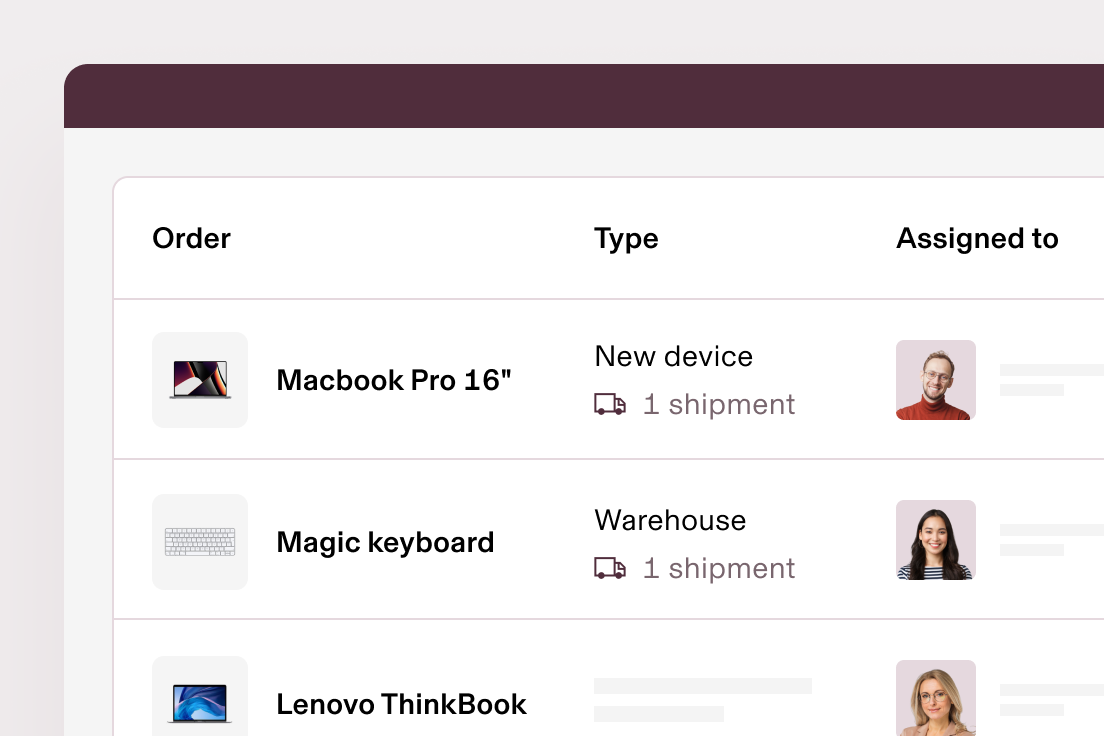
Order or reassign devices
Point, click, ship. With Rippling, you can order, reassign and ship devices directly to new recruits’ doors – all from a single location.
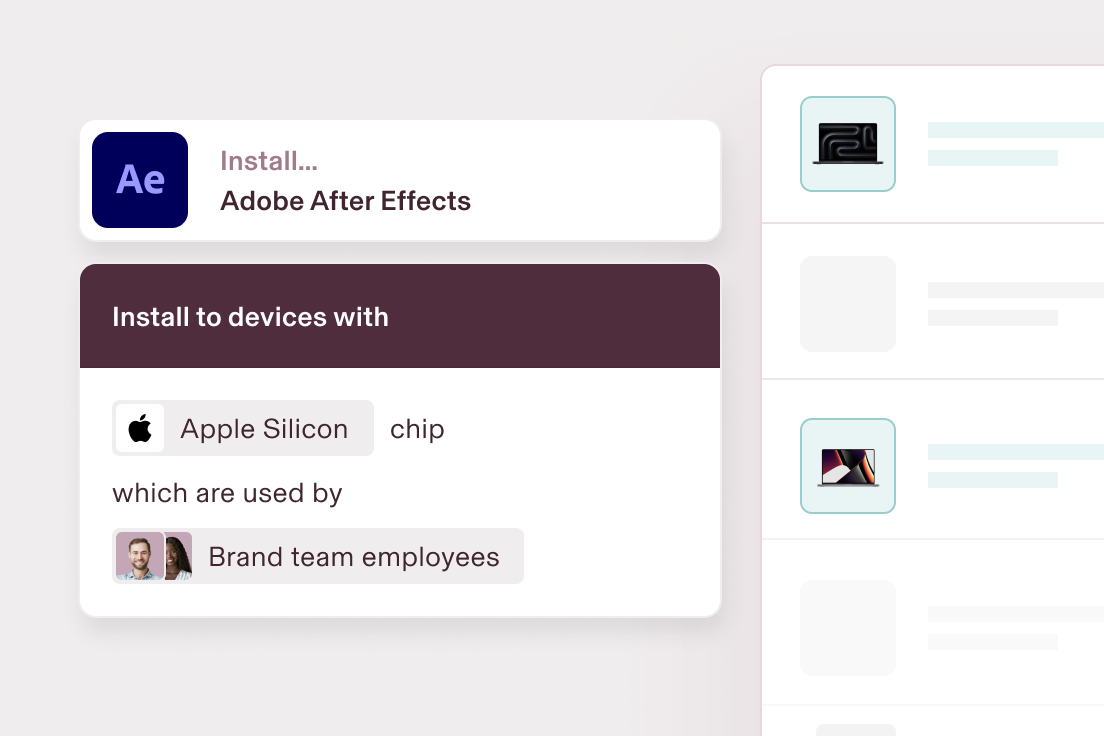
Automate device configuration
Hassle-free device enrolment. Automatically configure laptops, iPhones and iPads with the right software, access and security settings based on attributes like location, department or role.
Offboarding
Offboarding made secure
Retrieving employees’ devices can quickly turn into a security risk – especially if they’re remote. Rippling makes it easy by automating device offboarding, end to end.
Wipe and lock devices instantly
Because you’re automatically in sync with HR’s offboarding flow, you can schedule the exact time you want to lock and wipe a device.
Automate device retrievals
No more trips to the Post Office, messy delivery logistics or missing devices. Rippling automatically handles retrievals.
Securely store unused devices
Warehouse your devices in Rippling’s secure facilities around the world instead of messy IT storage rooms.


Inventory Management
We’ll handle the logistics
Our MDM is more than software. Rippling does the heavy lifting of fleet management, too.
Built different
Analyse, automate and orchestrate anything
Most “all-in-one” software consists of acquired systems. These modules are disconnected, so your business data is, too. Rippling takes a platform approach, building products on a single source of truth for all the business data related to employees. This rich, flexible data source unlocks a powerful set of management capabilities.

Permissions
Automatically govern what each person in your company can see, do and access.
Policies
Build custom policies that enforce your business’s unique rules and procedures.
Workflows
Automate virtually anything with hyper-custom triggers and advanced workflow actions.
Analytics
Make better decisions faster with real-time, unified data in an easy-to-use report builder.
END-TO-END security
All the security tools you need – and then some

Cross-OS MDM

Built-in endpoint protection

Zero-touch deployment

Custom script deployment

Device encryption enforcement

Audit logs

OS updates

Remote locking & wiping
And more
See all


SOC 2 Type II, ISO 27001, CSA STAR Level 2
Rippling combines enterprise-grade security features with regular audits to ensure that your data is always protected
Learn more about security and data protectionFAQs
What is mobile device management software?

Mobile device management (MDM) software is a solution that allows IT administrators and providers to securely manage and monitor mobile devices, such as smartphones, tablets and laptops, across an organisation. MDM software helps companies enforce security policies, track device usage, deploy apps and software updates, and remotely lock or wipe devices if they are lost or stolen. It ensures that corporate data is protected and that devices are compliant with company regulations.
What is MDM used for?

MDM is used to securely manage and control mobile devices within an organisation. Mobile device management solutions are primarily used for:
- Enforcing security policies like encryption, passcode requirements, and app restrictions.
- Managing device configurations, software updates, and settings with easy remote control.
- Tracking and monitoring devices for lost or stolen devices and protecting company data.
- Streamlining device provisioning and deprovisioning as part of the employee lifecycle (onboarding and offboarding).
- Ensuring compliance with company policies and regulatory standards related to mobile devices and data security.
How do I choose the right MDM solution?

Choosing the right MDM solution depends on a variety of factors unique to your organisation’s needs:
- Device compatibility: Make sure the MDm solution supports all the device types your organization uses, such as iOS, Android, Windows, and macOS devices.
- Security features: Look for robust security features such as data encryption, remote wipe, password enforcement, and the ability to track and locate devices in case of loss or theft.
- Scalability: Choose an MDM solution that can scale with your business as it grows. Make sure it can handle the number of devices your organization currently has and can easily expand as you onboard new devices and employees.
- Integration with existing systems: Select an MDM solution that integrates smoothly with your current IT infrastructure, such as HR, software management, or other endpoint management tools. Rippling, for example, integrates MDM alongside HR and IT management, streamlining onboarding, offboarding, and device management in one place.
- Ease of use: Consider how user-friendly the solution is for both administrators and end-users. A solution with an intuitive user experience and centralized management console will make it easier for your IT team to deploy, monitor, and manage devices.
- Cost: Determine your budget for MDM software and evaluate the pricing model. Some MDM solutions charge based on the number of devices or users, while others offer tiered pricing based on features. Ensure that the pricing aligns with the features you require.
How does MDM software enhance security for corporate mobile devices?

MDM software enhances security for corporate mobile devices by offering a range of features that protect sensitive data, ensure compliance and prevent unauthorised access, like:
- Device encryption: MDM software can enforce encryption on devices, ensuring that all data stored on mobile devices is securely encrypted, even if the device is lost or stolen.
- Access control: MDM gives organizations application management control to determine which apps and services can be accessed on mobile devices.
- Security policy enforcement: MDM helps enforce a variety of security policies, such as requiring complex passwords, setting up two-factor authentication, or ensuring devices have the latest security patches installed.
- App management and monitoring: With MDM, IT teams can deploy, update, and remove applications on mobile devices. They can also monitor app usage to ensure only approved apps are used, and malicious apps can be detected and blocked.
- Geofencing and location tracking: MDM allows companies to track the location of mobile devices and set up geofencing, so if a device moves outside of authorized areas, it can be automatically locked or wiped.
- Compliance and reporting: MDM software offers detailed reporting and auditing features, ensuring that devices are in compliance with corporate security policies and regulatory requirements.
By centralising management, enforcing security policies, and providing real-time monitoring and remote capabilities, MDM ensures that mobile devices stay secure, even in a highly distributed and mobile workforce.
What is Bring Your Own Device (BYOD) support?

Bring Your Own Device (BYOD) support refers to the practice of allowing employees to use their personal devices – such as smartphones, tablets and laptops – for work-related tasks. BYOD enables employees to access corporate resources, such as email, apps and files, on their own devices rather than relying on company-issued hardware. This approach offers several benefits, such as increased flexibility, cost savings and improved productivity, as employees can work from anywhere and use the devices they’re most comfortable with.

Manage your devices with Rippling
END-TO-END IT SOFTWARE
Native tools for the entire user and device lifecycle
All
Device management
Identity & access
Inventory management